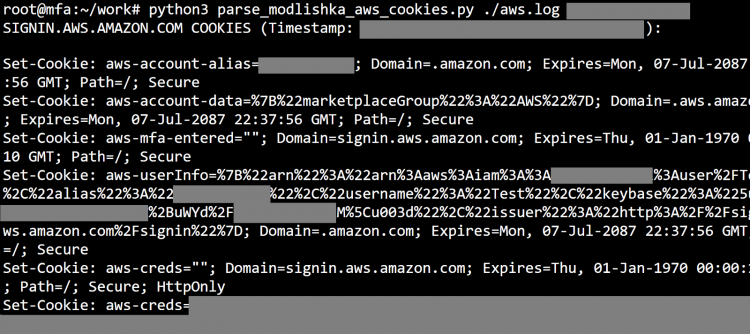
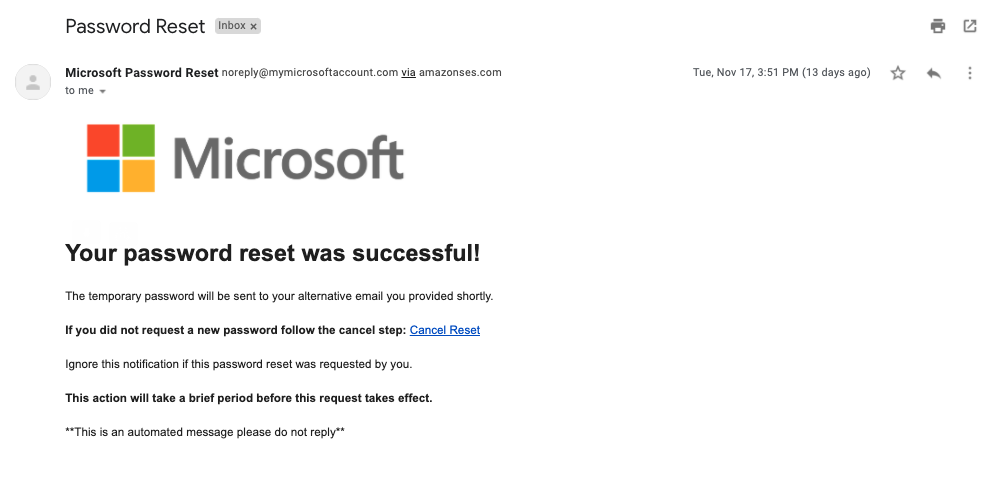
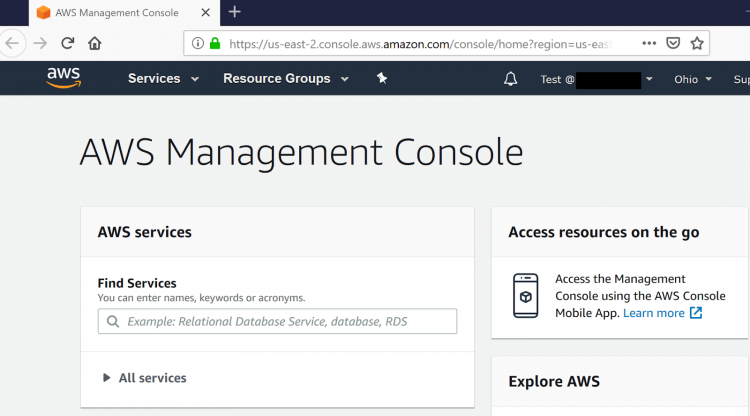
Examining Usable Security Features and User Perceptions of Physical Authentication Devices - ScienceDirect

Examining Usable Security Features and User Perceptions of Physical Authentication Devices - ScienceDirect

Examining Usable Security Features and User Perceptions of Physical Authentication Devices - ScienceDirect

Amplify incorrectly redirects some static images in a react.js SPA with trailing slash; others work correctly · Issue #1266 · aws-amplify/amplify-hosting · GitHub

Examining Usable Security Features and User Perceptions of Physical Authentication Devices - ScienceDirect